It is now a universal truth that we spend a significant part of our personal and corporate life in the virtual world. Everything from our personal identity, personal relationships to corporate relationships are up there in cyber space, within easy access for anyone with the required intent and tools.
This also means that traditional notions of risk as a “damage to physical property” has now been replaced by even more dominant threat of damage to our cyber assets and identity. Elections are won or lost, nations are besieged and corporate battles are waged in cyber space.
The information security industry releases appropriate patches and fixes to emerging threats, but often this is done post-facto, after huge damage has already been inflicted on organisations. Malignant agencies and hackers are one step ahead of us in discovering vulnerabilities in the technology portfolio of their prey. This poses a challenge for business leaders to develop a comprehensive approach to protect the information technology assets against malignant attack.
Every CIO should keep abreast of the latest technology assets deployed in their company and keep an eye out on the risk profile of their information assets. Threats could emerge from data centre infrastructure, people, network, data or system code. However, it is not practical to expect that every company can mitigate all possible risks. Hence, cyber security insurance is emerging as a key financial instrument to provide cover against uncontrollable cyber risk.
Types of cyber risks
Major types of cyber attacks that happen to an organisation can be summarised as follows:
- Brute force attack: Software or an algorithm (e.g. robots) which is written to attack a system by searching for vulnerabilities and attacks a password-protection mechanism.
- Social engineering/cyber fraud: A typical case of social engineering cyber fraud where the attack is on individuals and policies of an organisation.
- Distributed Denial of Service attack (DDoS): Overloading of a server with connections, with the aim of shutting down the target’s website or network system
- Phishing attacks: Hundreds of emails with an attachment or link are sent in an anticipation that someone will click on these links/attachments, allowing the hacker access to take control of the system.
-
Malware, spyware, ransomware: Malicious
software created with the intent of gaining
an unauthorised access including uploading
of viruses or spyware.
- Lost time and productivity
- Remediation time
- Cost of purchased technologies
- Cost of outside consultants and technologies
- Short-term damage to reputation, brand and image
- Loss of revenue
- Cost of notification
- Out-of-pocket costs to prevent harm to victims
- Lost customers
- Regulatory fines and lawsuits
- Long-term damage to reputation, brand and image
- Data breach insurance
- Network security liability insurance
- Restoration costs for data and programs
- Business interruption
- Media liability
- E-payment liability
- Hacker theft cover
- Crisis communication
- Does the insurance policy cover major areas of risk exposure for the organisation?
- Is the policy standalone or an extension to an existing policy?
- Is the policy customised to the specific needs of the organisation?
- What is the extent of coverage to first-party and third-party service providers?
- Does the policy cover malignant attacks by insiders and employees?
- Does it cover a suitable period between actual breach and the date of detection of the breach?
- Are the costs for recovery covered?
- Maturity of IT project delivery, specifically for IT security
- Adoption of best practices such as NIST/COBIT
- Deployment of IT security management tools
- Level of awareness among employees
- Adherence to clearly defined policies for safeguarding IT security
- Governance processes e.g. periodic audits and vulnerability tests
Damage from cyber attacks
Cyber attacks can inflict significant financial damage to any organisation. The type of damage could be any of the following:
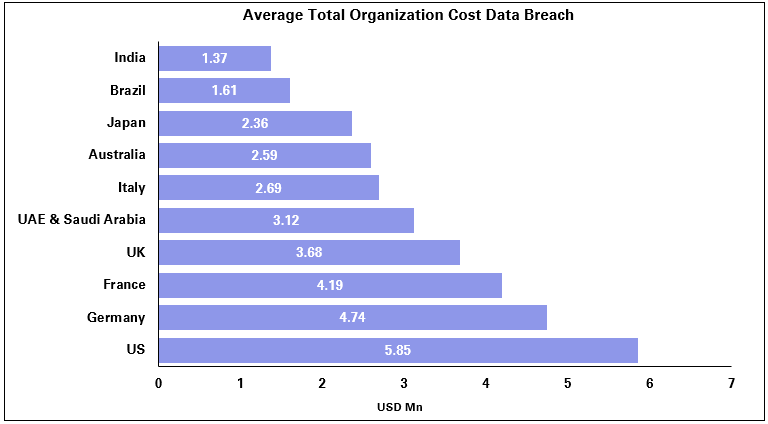
Unlike risks in the physical world, cyber attacks can proliferate instantly and cause a disproportionate level of damage. As shown in the graph above, the cumulative cost of just one of these risks (data breach) runs into billions of dollars.
Over the last few years, large banks have experienced a number of cyber attacks and failures:
• Cyber crimes: In 2013, hackers stole £1.3 million by hijacking the computer system of a branch of a British Bank.
• Data breach: In 2015, a bank paid £5 million in compensation to 2,000 customers whose personal data was stolen from a bank. Also, in 2017, Bupa suffered a data breach affecting 500,000 customers on its international health insurance plan.
• Technical glitches: Through 2015, a bank was affected by technical glitches caused by malignant sources. This included online and shop refusal glitches, ATM and money withdrawal glitches and complete digital channel glitches.
• Electronic record storage failures: Barclays was fined £2.3 million by the US Financial Industry Regulatory Authority (FINRA) in 2014 for one such widespread failure. Such records must be kept for a period of at least 10 years, to protect investors.
• Blocking access to accounts: Lloyds Banking Group suffered 48-hour online attack in January 2017 as cyber criminals attempted to block access to 20 million UK accounts.
• Fraud: In 2011, 360,000 Citi accounts were hacked and about $2.7 million were stolen.
So the demand for cyber-security insurance has been growing exponentially in the last few years. The global market for cyber security insurance is estimated to grow to more than $20 billion by 2025. The insurance industry has designed several products to address specific types of risks. Some of the products are as follows:
Guidance on buying insurance cover
Despite the magnitude of risks from cyber threats, there is very low awareness at board level about the potential ways of mitigating cyber risks. This is partly due to the technical nature of the product, and partly due to the unavailability of standardised products. Cyber attacks that made global news headlines helped in raising the level of awareness of these risks. After the WannaCry attack in May 2017, which paralysed hospitals in the UK and disrupted transport networks, AIG Asia reported an 87% YoY increase in demand for cyber insurance compared to the same period last year.
"Decisions about cyber insurance need close collaboration at board level"
Cyber insurance tends to be a bespoke solution for every organisation. Business leaders should ask and review the following questions when selecting cyber risk cover:
An industry survey indicated that policy premium and the breadth of coverage were the two most important factors that determined the choice of cyber insurance coverage. However, cyber security insurance requires careful consideration of a much wider array of factors. If the organisation does not have internal skills to address these questions, it is advisable to engage a specialist insurance broker who can hand-hold the organisation from purchase of the policy to assistance in getting the claims paid.
Focus areas for underwriting cyber insurance
The unique nature of every client’s IT portfolio also poses a challenge for insurance companies to estimate the risk and underwrite a suitable cover. A cyber insurance provider, like any other insurance company, needs do a pre-assessment of the organisation in terms of its risk profile and risk governance.
By investing in the tools, processes and teams required for ensuring cyber resilience, business leaders can protect the organisation against catastrophe and prepare for a secure future.
To read more such insights from our leaders, subscribe to Cedar FinTech Monthly View